Implementation of the NIS2 Directive
To ensure a fast and robust implementation of the NIS2 Directive requirements, Leave a Mark Consulting Group offers flexible solutions through multi-competence teams. This means you gain access to specialists with broad and complementary expertise, working together to deliver results efficiently and competently.
About the NIS2 Directive
NIS2 (Network and Information Systems Directive 2) is an EU directive aimed at strengthening cybersecurity across member states. While the directive forms the foundation for Danish legislation in this area, it is the Danish implementation laws that are legally binding — and therefore the most relevant starting point for compliance efforts.
The directive targets organizations in critical sectors, including energy, transport, healthcare, finance, water, and digital services such as cloud providers and online marketplaces. These organizations are required to establish a high level of cybersecurity, with a strong focus on risk management, preparedness, and the reporting of serious incidents within 24 hours.
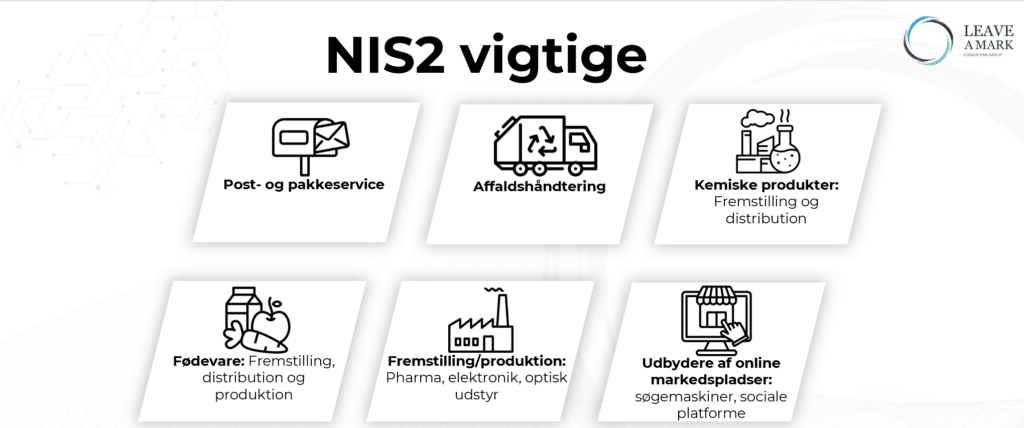
See below which organizations are subject to the directive.
We Help Ensure Your Organization’s NIS2 Compliance
Leave a Mark Consulting Group is recognized for its in-depth expertise in cybersecurity, risk management, and regulatory compliance. Our team brings proven experience in implementing complex security standards across sectors — with a strong focus on aligning with the demands of the NIS2 framework.
We take a practical, results-oriented approach. By assessing your organization’s risk profile and pinpointing key vulnerabilities, we customize the implementation process to meet legal obligations while minimizing impact on daily operations and resource use.
Would you like to learn more about the NIS2 implementation process?
The essential entities

The important entities
Implementation of NIS2 in Danish Legislation
The NIS2 Directive has been fully implemented into Danish law and is specified through three key acts, each applicable to different sectors and types of organizations:
The act on measures to ensure a high common level of cybersecurity (NIS2 Act) – Applies to the majority of covered businesses and institutions. It outlines requirements for risk management, incident handling, executive responsibility, and regulatory oversight.
The act on enhanced emergency preparedness in the energy sector – Specifically targets entities within the energy sector, focusing on resilience, security, and emergency preparedness planning.
The act on security and preparedness in the telecommunications sector – Imposes specific obligations on telecom companies and other relevant communications providers, covering cybersecurity and supply security.
These laws form the legal framework that Danish organizations must comply with. That is why our advisory services are always rooted in the concrete requirements and expectations set by Danish authorities through legislation.
Organizations are required to document their cybersecurity efforts, establish clear procedures, and demonstrate continuous compliance. Supervisory authorities have the power to conduct audits and impose directives or sanctions in cases of non-compliance.
What are the requirements of NIS2?
In Denmark, the NIS2 Directive has been implemented through specific national legislation — including the NIS2 Act, the Telecommunications Security Act, and the Emergency Preparedness Act for the Energy Sector. These laws impose heightened obligations related to governance, risk handling, and reporting duties, covering both technical systems and organizational structures.
The following requirements are among the core elements of the Danish implementation:
- Executive Responsibility: Executive management holds the overall responsibility for ensuring that the organization complies with cybersecurity requirements. Management must be informed about the organization’s risk exposure and ensure that appropriate measures are implemented.
- Risk Management: The organization must identify and assess relevant cyber risks and implement both preventive and corrective security measures — including within the supply chain.
- Business continuity and incident response: Emergency plans, system recovery procedures, and a crisis management structure must be established to handle serious incidents effectively.
- Regulatory reporting: Significant security incidents must be reported to the relevant authorities within 24 hours and continuously updated with additional information within 72 hours.
NIS2 implementation process: A step-by-step guide
Preparation and Risk Assessment
Phase one focuses on assessing your existing cybersecurity landscape and determining the specific aspects of the Danish NIS2 legislation applicable to your organization. This includes a high-level Business Impact Analysis (BIA) targeting the systems and business areas most vital to your operations.
Strategic Planning
Drawing on the results of the analysis and your existing security maturity, we create a tailored implementation plan. This plan incorporates both technical and organizational considerations and is anchored in the Business Impact Analysis (BIA).
Deployment and Implementation
We assist in implementing the necessary security measures, policies, and procedures — including incident response, access control, and supply chain security — to ensure effective compliance with the applicable Danish NIS2 requirements.
Operations and Maintenance
We implement processes for the continuous maintenance of security measures to ensure your organization remains protected against constant and evolving threats. As a general recommendation, we advise evaluating the threat landscape twice a year to identify any new threats and implement appropriate measures to mitigate their impact.
NIS2 Statement
A NIS2 Statement from Leave a Mark Consulting Group documents that your organization meets the requirements for cybersecurity, incident handling, and risk management. The statement is based on a thorough GAP analysis and a review of your existing documentation and practices.
The benefits of a NIS2 statement include increased credibility, enhanced security, and strengthened competitiveness.


