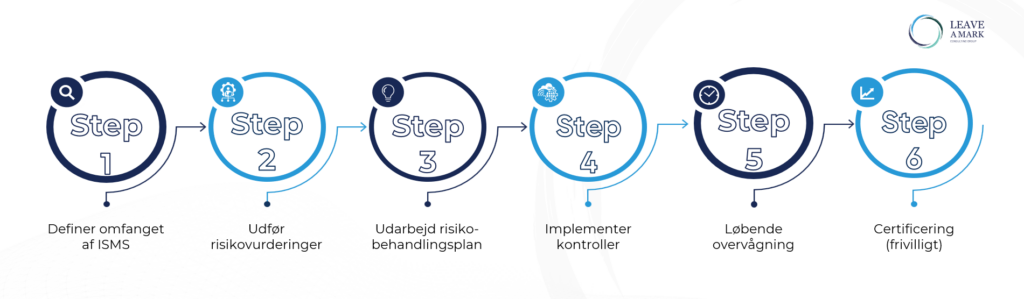
Why chose ISO 27001?
All companies have fire and burglar alarms installed to prevent major operational threats. But data and information security should be weighted at least as high. Not only that corporate customers has a high risk if information security is not in order, there is now introduced a number of regulations gives a high fines and punishment if data is not protect correct.
With an ISO27001 certification, the company gets a first-class management system so that the quality, safety and efficiency are top.
At the same time, an ISO27001 certificate contributes to promoting international trade, and up to 85% of all corporate customers sees certification as confidence-building.