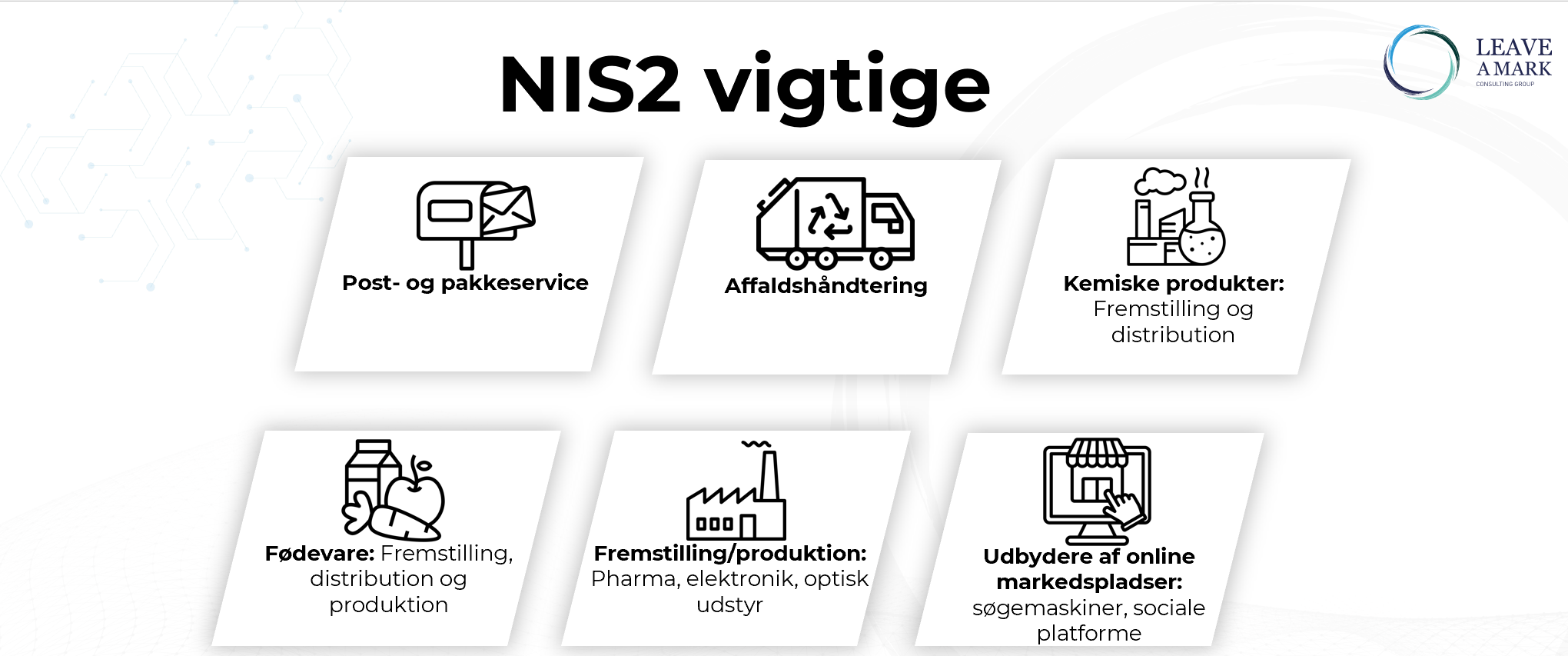
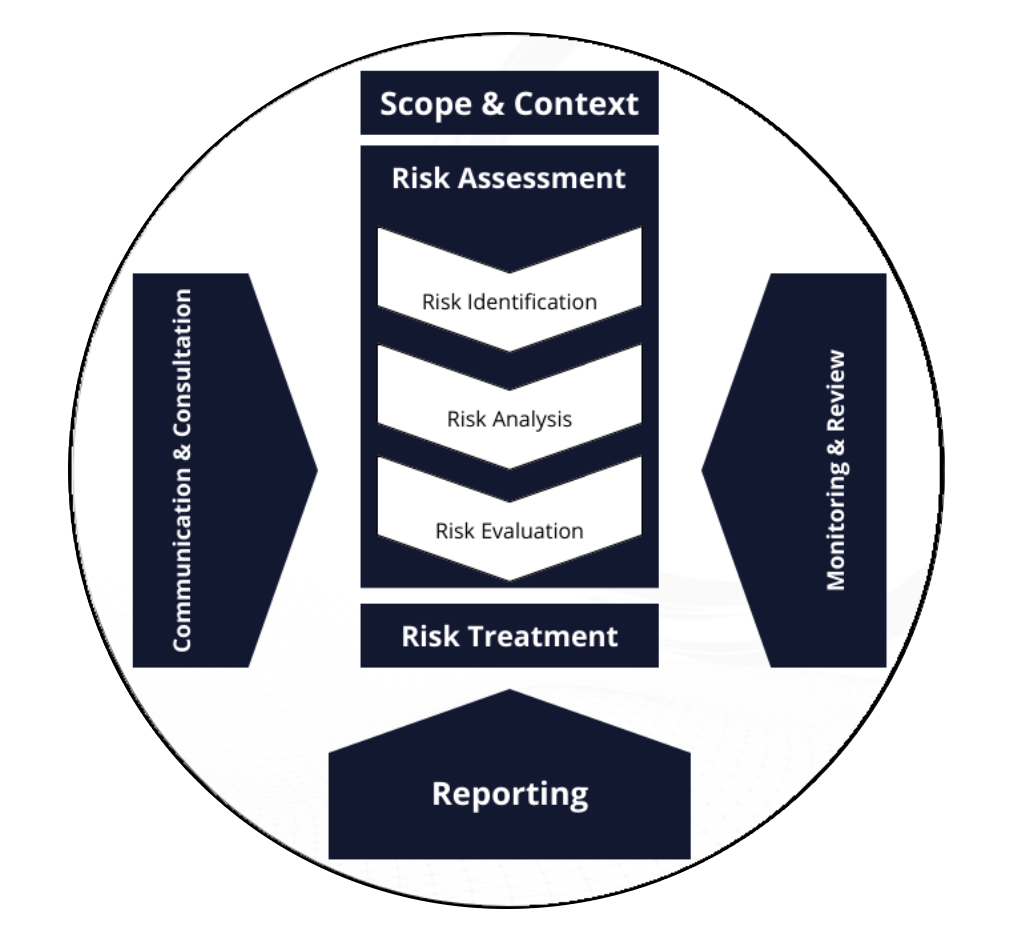
In this phase, we utilize the results from the previously conducted Business Impact Analysis (BIA) along with your organization's current IT security to develop an implementation plan. The implementation plan is designed to address both the technical and organizational aspects of cybersecurity.
At the technical level, the plan may involve updates to existing IT infrastructure, implementation of advanced security solutions, and configuration of network protection. This could entail installing firewall systems, intrusion detection/prevention systems, antivirus software, and other tools to safeguard against cyber threats. Additionally, we will ensure that these technical measures adhere to applicable standards and guidelines.
At the organizational level, we will focus on developing or adapting policies and procedures that are fundamental to NIS2 compliance. This may include the development of clear guidelines for handling security incidents, establishment of an emergency response plan, and training employees in security procedures and best practices.